How to Get Information About Linux Commands and the PATH Variable
How to Get Information About Linux Commands and the PATH Variable One of the essential aspects of Linux is the command line, which allows users
How to Get Information About Linux Commands and the PATH Variable One of the essential aspects of Linux is the command line, which allows users
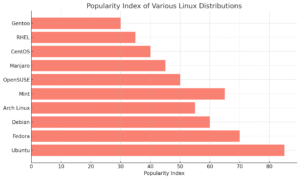
As the Linux ecosystem evolves in 2024, many popular distributions continue to shape the open-source landscape, each offering unique strengths. From the user-friendly Ubuntu to the cutting-edge Fedora and the highly customizable Arch Linux, there’s a distro for every user type. Following the end of life for CentOS, new alternatives like Rocky Linux and AlmaLinux have emerged, providing enterprise-grade stability. This guide dives deep into the top 10 most popular Linux distributions, outlining key features and use cases to help you find the best fit for your needs. Explore more at Admirux.com.
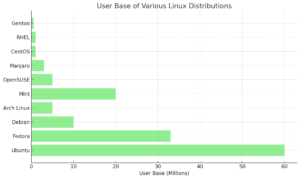
Linux distributions have become a vital part of the open-source ecosystem, offering solutions for everyone from casual users to enterprise IT professionals. This article explores the user base of popular Linux distributions like Ubuntu, Fedora, and Linux Mint, revealing why some distros dominate the market while others cater to niche needs. Whether you’re a beginner or an experienced user, discover the best Linux distro for your needs using the Admirux Distro Picker Tool. Dive into the trends shaping the future of Linux and find out which distribution is right for you.
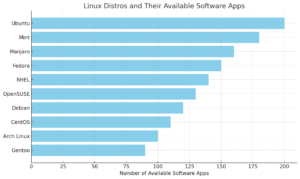
When choosing a Linux distribution, the availability of software applications is a critical factor that can greatly impact your experience. This blog post explores the software ecosystems of ten popular Linux distros, including Ubuntu, Mint, Manjaro, Fedora, and more. It delves into why some distros offer more software options, how package management systems differ, and provides guidance on selecting the right distro based on your specific needs. Whether you’re a beginner, developer, gamer, or enterprise user, understanding the strengths and limitations of each distro can help you make an informed decision.

In today’s rapidly evolving digital landscape, cybersecurity is more critical than ever. The National Institute of Standards and Technology (NIST) Cybersecurity Framework (CSF) stands out as a vital tool for organizations looking to strengthen their cybersecurity defenses. Unlike other frameworks, which often focus on broader IT governance, the NIST CSF is dedicated exclusively to cybersecurity. It provides a flexible, accessible, and effective approach to managing cyber risks, making it an essential resource for businesses of all sizes.
The NIST CSF is structured around five core functions—Identify, Protect, Detect, Respond, and Recover—each representing a key aspect of cybersecurity risk management. This framework is not only comprehensive but also adaptable, allowing organizations to tailor it to their specific needs and industry requirements.
Compared to other frameworks like ISO 27000, COBIT, and SABSA, the NIST CSF’s exclusive focus on cybersecurity gives it a unique edge. Whether you’re a small business or a large enterprise, implementing the NIST CSF can significantly enhance your cybersecurity posture and ensure your strategies align with broader business objectives.
For more insights on how to effectively implement the NIST CSF and strengthen your cybersecurity strategy, explore our resources at ADMIRUX.com.

In the ever-evolving landscape of cybersecurity, a strong defense strategy is essential for safeguarding your organization against a growing list of threats. This comprehensive guide explores key security measures, including incident response plans, compensating controls, deterrent controls, and detective controls, through real-world scenarios. Learn how these components work together to build a resilient cybersecurity strategy that not only prevents attacks but also prepares your organization to respond and adapt to any challenges. Explore practical examples and insights to enhance your understanding and implementation of these vital security controls.